Cybersecurity Solutions
Our solutions are designed to safeguard substation automation systems against the evolving landscape of cyber threats, ensuring the integrity and reliability of the Smart Grid.
Evolving to Smart Grid Technologies
As power generation, transmission, and distribution networks evolve into Smart Grid technologies, they embody the future of electrical power systems. These systems prioritize reliability, flexibility, efficiency, and environmental sustainability. However, this evolution brings challenges, especially in cyber security, potentially impacting the smooth operation of substations and the broader grid.
Adhering to IEC 61850-5 and IEC 62351-6 Standards
Our focus aligns with IEC 61850-5 and IEC 62351-6 standards, detailing communication models and essential security mechanisms for modern substations. Recognizing the long lifespan of primary substation equipment and more frequent updates of secondary equipment and Intelligent Electronic Devices (IEDs), our solutions emphasize a domain-specific data model, ensuring interoperability and resilience against rapid changes in communication technology.
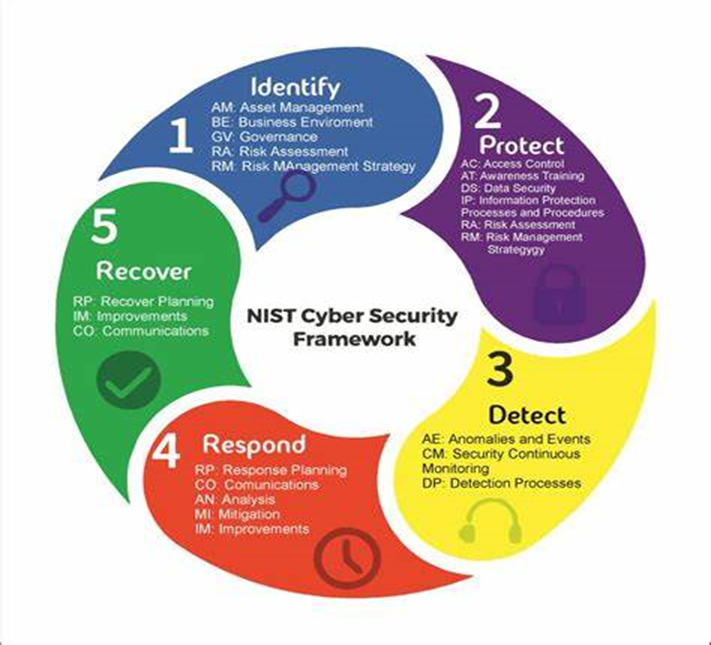
Comprehensive Cyber Security Solutions
We provide advanced cyber security solutions tailored for Industrial control systems (ICS). Our offerings include:
Application Security Solutions
We ensure the robustness of software applications from development to deployment, protecting against vulnerabilities and attacks. Our tools span from routers for network protection to vulnerability scanners, securing both software and hardware layers.
Endpoint Security
Covering servers and workstations, our solutions detect and mitigate malware, unauthorized access, and breaches. Key components include:
- Endpoint Protection Platform (EPP)
- Endpoint Detection and Remediation (EDR)
- Extended Detection and Response (XDR)
Network Security
Our tools monitor network traffic to identify and counteract malicious activities. This includes:
- Network Access Control
- Network Segmentation
- Network-Based IDS (NIDS)
IoT Security
As IoT devices proliferate, we provide tools for network security, encryption, and authentication, ensuring the integrity of mission-critical applications and sensitive data.
Cloud Security
Managing security in complex cloud environments, our tools detect and address security lapses and vulnerabilities. Solutions include:
- Cloud Access Security Brokers (CASB)
- Cloud Workload Protection Platform (CWPP)
- Cloud Security Posture Management (CSPM)
Centralized Cyber security solution
- Local Active Directory solution
- Backup and Recovery Management
- Antivirus Patch Management
- Whitelisting
- Patch Management
- Network Management
- End point security
- AAA solution
- 2 Factor Authentication
Technology Partner Names












